This is a text automatically translated from Italian. If you appreciate our work and if you like reading it in your language, consider a donation to allow us to continue doing it and improving it.
Content index
- Tor Browsers, who is he?
- Guide to using Tor Browsers
- How does Tor work?
- Installation
- Let's get to the heart of things and dispel some myths
- The dark web
- Tips for improving anonymity security on Tor
- Guide to using Tor Browsers
- Guide to using Tor Browsers: the points to follow
- The VPN dilemma
- Guide to using Tor Browsers: conclusions
- Guide to using Tor Browsers: some important links
This Guide to using Tor Browsers was written by DebianMan For TheAlternatives. You can also visit his Youtube channel called Linux world.
ATTENTION! This writing (Guide to using Tor Browsers) it is not intended to be complete nor to replace the official Tor guides. The guide is intended as a summary explaining the nature of Tor and above all as a decalogue for using it correctly and safely.
To have all the complete documentation, please refer to the official Tor sites which you will find in the link at the bottom of the article.
THE GUIDE IS NOT INTENDED TO BE IN ANY WAY AN INVITATION TO CARRY OUT ILLEGAL ACTS BY EXPLOITING THE TOR NETWORK. THE AUTHOR IS IN NO WAY RESPONSIBLE FOR AN ILLICIT USE OF TOR BY USERS.
Tor Browsers, who is he?
Tor is, to put it simply, an Internet networking protocol designed to anonymize data transmitted through it 1. The use of Tor's software will make it difficult, if not impossible, to trace the true identity of those who browse and it will not be possible to tell which country they are in by analyzing the IP address, which can be very useful for journalists, activists, men of business and more. In fact, it is above all these categories that exploit the Tor network to protect information and remain invisible as much as possible. But there is also a large group of "ordinary" people who use Tor simply to defend their identity.
“This is the world we live in: people rely on the mistakes of others to manipulate each other and use each other… and also to relate.”
(Mr. Robot)
Tor is used through a Browsers based on Firefox, called precisely Tor Browsers, where Tor stands for The ORnion Router.
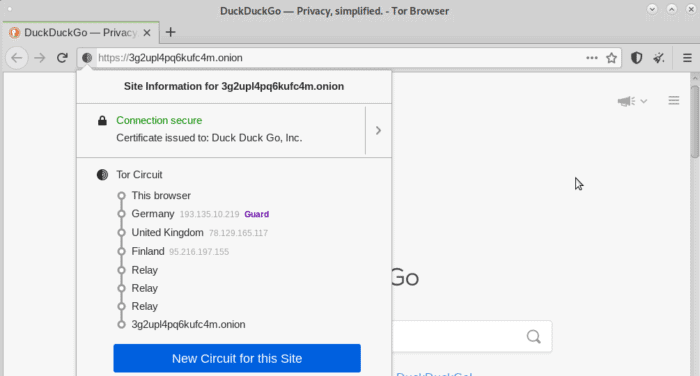
It is used, among other things, also to access (always via an encrypted connection) in the so-called Dark Web, that is, that hidden part of the web, which is not indexed and accessible by a normal person Browsers and whose sites do not have a classic URL, but a random alphanumeric sequence and the .onion: for example, the onion version of the Search engine Duckduckgo And 3g2upl4pq6kufc4m.onion.
Some sites, as in fact Duckduckgo (but also Facebook, The New York Times, Protonmail and others) have their own onion interface alongside the “normal” version; while other sites are born only as onions and are more difficult to trace given that the URLs (as we have just seen) are random and, in certain circumstances, change with a certain frequency to be less identifiable.

Guide to using Tor Browsers
Leaving aside what can be hidden among the onion sites, between illegality, legality, activism, journalists, clandestinity and businesses of various kinds, it is my duty to advise a certain prudence, given that on the hidden web you can find everything: falling into a bad situation even just for giving in to a curiosity, I'm not saying it's easy but it's possible.
It must be said that those who claim that the dark web and onion sites are only places of perdition and crime are in bad faith. Anyone, even for noble purposes, can exploit the hidden part of the internet. Obviously the network is free and, if hidden, it is natural that criminals of all types also exploit it to their advantage. I'll reiterate the point going forward.
Let's also take into account the fact that the vast majority of people who browse with Tor do so to visit standard sites (not onions, so to speak) which they could easily visit from any Browsers, but use Tor just to have a little more anonymity.
How does Tor work?
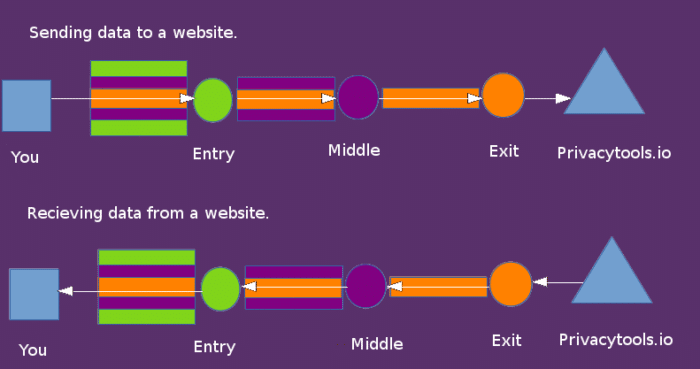
The way Tor works, in short, is as follows: from our workstation (our PC or phone or tablet) we normally connect to the desired site through a direct connection (in reality we also go through other servers but that's the concept).
In Tor, however, our connection goes through three knots (or relay) of the onion network which encrypt the outgoing traffic three times (how many nodes there are) to be decrypted in the last step when it reaches the site.
Outgoing traffic is decrypted because otherwise the site would not be able to "understand" the request and therefore give us back what we are looking for, i.e. the site itself.
In more detail, the passage of traffic through the nodes occurs through step-by-step decryption:
- The first node (also called guard knot) has three layers of encryption;
- in the transition to second node he will take one away;
- from the second to third node the second layer will be removed;
- the third and final layer is removed outgoing from the third node to the site.
In this way our IP will be hidden and the site will see the IP of the third node
The layered system also reveals why the network is called onion!
The three-node system is made so that no node knows what another node knows:
- the first knows who we are BUT NOT WHERE WE GO;
- the third knows where we are going BUT NOT WHO WE ARE;
- the second node acts as an intermediary: it knows where the traffic came from (first node) but it knows neither WHO WE ARE nor WHERE WE ARE GOING. Its role is to prevent the first and third from coming together and forming a complete user identity (WHO IS HE AND WHERE IS HE GOING).
The site finally sends the traffic back and allows us to view the site.
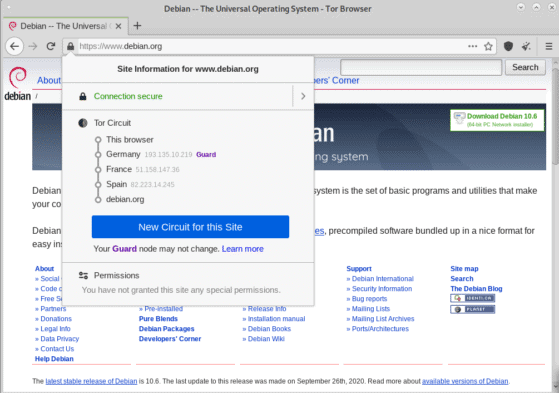
Translated into graphics we can concretely see how the "onion" is gradually browsed until it is completely uncovered and how the traffic is brought back to the user.
In practice this is how from Tor Browsers we can view the nodes that have currently been assigned to us for the site visited (in this case debian.org):
Installation
The installation, once downloaded from the official website, for Windows and Mac follows the classic procedure of double-click the exe file (for Windows) or dmg (for Mac) and follow the procedure.
For Linux it is still simple but different and doesn't actually involve a real installation: you download the tar.xz compressed file from the official website by extracting the folder tor-Browsers_en-US (here we mean the American English version); copy the folder to a path that allows the automatic inclusion of Tor in the applications list: it is more a matter of convenience and to avoid keeping the folder in the Downloads. Typically the following path is chosen: home/user/.local/share/applications. You then copy the folder to applications. Once the folder is open, double click on Tor Browsers Setup and Tor will start. For configurations and use, continue to follow the guide.
On Android just download theapk from the PlayStore It installs automatically like any app.
On iOS it will be like all the apps but you will have to turn to a replacement app called Onion Browsers, available in App Store. To know more: https://blog.torproject.org/tor-heart-onion-Browsers-and-more-ios-tor
The advice, iOS aside, is to download ONLY AND EXCLUSIVELY from the official website: https://www.torproject.org/download/. For Android you can download the apk either from the Play Store or from the Tor site.
Let's get to the heart of things and dispel some myths
First of all, contrary to what some say, Tor is NOT paid. It is not from PC, be it Windows, MacOS or Linux and not even in the mobile version. There is a section for donations but it is certainly not the only project that legitimately asks for the support of its users. But making the offer is optional. Proof of the fact that Tor is not paid, there is the indisputable fact that offers can also be made in complete anonymity: how could it Tor, if it were paid, can you trace who made a payment in cryptocurrency (perhaps using a network other than your own)?
Tor was created by the government and therefore definitely contains a backdoor to spy on users 2.
Tor's code was not written by the US government, but by Roger Dingledine and Nick Matthewson, with resources from the Navy's research laboratory. The claim that it must therefore contain a backdoor does not hold water for the following reasons: First, the US government uses Tor to hide its activities: if it had a backdoor, it would not be safe to use it.
One could argue that the government could create its own anonymity systems, but that would defeat the whole point: if the government built its own system and only let itself use it, then ALL traffic would automatically be known to be CIA/NSA/FBI traffic , which would make it useless. Let us remember well that one cannot be anonymous alone, but it is necessary to form a sufficiently large crowd in which to blend in. The more people enter the fray, the more difficult it is to find an individual.
Using Tor puts you on a blacklist 2.
The claim that using Tor gets you on a watchlist in a democratic country is implausible. Not because it can't happen, but because it would be pointless even if they did.
The Tor network receives approximately 2.5 million users daily. It's a large list, large enough to make targeted surveillance impossible. The only place where using Tor could be dangerous is in nations run by oppressive governments and where freedom is severely restricted, but in this case even a VPN is likely to arouse suspicion and land you on the “list” . With Tor, among other things, you can try to avoid being discovered by using bridge relays (we'll see what these are shortly). Finally, it is worth considering what using Tor protects you from and whether this is more important than what the non-imaginative but still entirely theoretical “list” would expose you to. It's a bit like thinking that using an antivirus, firewall or HTTPS will get you on a list, so you won't use any of these tools to protect yourself anymore.
“Tor is slow”. Maybe it's true, but Tor is not designed to navigate as if you were on a Browsers "standard". The connection passes through three nodes which can also be distant from each other and from our position: if I am in Milan and Tor connects me like this: USA-Japan-Canada it is obvious that navigation will not be fast. If instead the circuit is Switzerland-France-Germany then I will probably always be slow but not that slow.
Another reason for slowness may be the congestion of some nodes even if they are close to us. In any case it is always possible to change the node circuit using a specific button from the Browsers until we find what satisfies us. However, compared to a few years ago, the speed has improved a lot.
Going forward, many say that the hidden network is a repository for viruses. False! You don't get more viruses on the dark web than you can on the regular internet. Indeed, perhaps even less: those who spread viruses aim to target large numbers. Now, it is indisputable that the clear net has a much, much larger user base than the dark net.
Last but not least: Tor is NOT illegal and it is not a tool for criminals. Is a kitchen knife illegal? No, and if it is used to kill someone it always remains a neutral instrument. Is the car illegal? No, and if a madman rushes into a crowd at 200mph and causes a massacre, the car always remains a neutral instrument. Same for the Internet and specifically for Tor: there are many who exploit it for illicit activities. So what?
So using Tor to view standard sites to protect your anonymity is fine: it's not the easiest way but it's doable and above all legal.
Onion sites and the dark web are not synonymous with illegality: as mentioned above, many sites existing on the surface web have their onion equivalent without being illegal and in any case Tor is mostly used to view "standard" sites. The dark web can also be an instrument of freedom, where freedom of speech is denied and journalists and activists are at great risk.
Do you want to open an onion site? It can be done and no one will put you in jail! An onion site is a site and that's it! can be about state secrets like recipes for apple pie! At most you won't be as well known as if you made a site on the surface web: making a recipe site on the dark web would be a bit stupid, don't you think? Rather than tortedeliziose.it your site will be something like df6yje3l9rxq2dnz.onion. I don't think it's very productive.
They say in general that those who use Tor, Signal and encryption tools is because it has something dirty to hide. Some no doubt, but the question is: how many of you keep your front door wide open? You have nothing to hide anyway, right? Here, the concept translated into a nutshell is this. Privacy and security are rights that have nothing to do with wrongdoing. Anyone who says otherwise probably has something they don't want to tell us!
The dark web
A note linguistics: the term dark web it simply means dark, hidden, unseen network. However, in English dark also has the meaning of dark, evil, sinister, etc. The fact that in dark web criminal trafficking of all kinds has taken place over time, has brought the meaning of the original term towards its negative meaning. So today, very superficially, that is dark web like evil web. But the story is in very different terms!
It is also good to define the terms dark web And deep web, often used as synonyms but which actually represent two different realities. The deep web is everything that is not indexed by search engines. An example? A Facebook page visible only to friends. Or a portal whose content is only accessible through a login. In short, everything that cannot be returned directly to us Search engine whatever it is.
The dark web is a minority part of the deep web but only accessible through Tor and which is essentially represented by .onion sites.
Tips for improving anonymity security on Tor
And here we come to the practical and perhaps most important part to make the best use Tor without making mistakes that could blow our protection.
Tor it does not protect us 100%, just as a VPN or any other defense system (for example an antivirus or a firewall) does not protect us 100%. Protection and security depend on many factors and a variety of user behaviors. Tor has some critical issues like all software, but its structure is fundamentally safe: the people who were discovered, in the majority of cases, committed carelessness and banal behavioral errors.
Guide to using Tor Browsers
You know the hacker from the movies who enters the Secret Service site without being discovered and then brags on Facebook? Here, this, as incredible as it may seem, is one of the methods with which the police pinch the filibusters.
Then agencies and police have a whole series of extremely sophisticated tools to trace the identity of users, but personal error is usually the door from which they gain access. It remains basic that any de-anonymization (sorry for the bad anglicism, but it's to be clear) does not happen by breaking the Tor encryption, but by bypassing it by exploiting flaws in the Browsers or, as just mentioned, thanks to errors on the part of unwary navigators. Now, I imagine none of us need to fear the Police, Carabinieri and GdF, but de-anonymisation can also take place at the hands of users malicious. Bespectacled, pimply hackers who may have launched a challenge between friends to see who among them can find more passwords than unsuspecting users. Science fiction? Not so!
So let's see how to cook our onions correctly without burning them.

Guide to using Tor Browsers: the points to follow
- Increase the security level from basic to medium or maximum through the shield icon or the mobile version menu. By increasing the level of protection you will have greater difficulty on some sites due to the lack of certain blocked functions, but security benefits. The 3rd level of maximum security locks you down even more. There, however, you really risk not being able to see a lot of sites, even if, on the other hand, you will have much more complete protection.
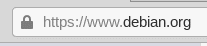
- Visit HTTPS sites only and avoid HTTP like the plague. Tor already has a default plugin that pushes HTTPS while avoiding HTTP when possible but be careful anyway. If the final node, which decrypts traffic and is Tor's real Achilles' heel, is run by malicious actors or government agencies, HTTP will be a way to spy on you, steal information and potentially trace it back to you. Bear in mind that most sites are now in https, but it's a good idea to keep your eyes open. HTTPS uses a series of cryptographic protocols called Transport Layer Security. It is not necessary to know the details, this is not the right place: for those who want to delve deeper into the topic I recommend the following guide: https://siamogeek.com/2013/08/https-come-funziona/.
All you need to know is that whenever there is a lock and the https prefix in your address bar, your Browsers will encrypt the data in a way that can only be decrypted by the destination server:
- Never use JavaScript and Flash unless absolutely necessary, possible vehicles for attacks and intrusions. Tor by default has Flash disabled and has a plugin, NoScript, which manages and blocks scripts, so we are basically already protected. Furthermore, by setting the maximum security level (see above) Java is disabled practically everywhere. If you want you can type config:about in the address bar, search for javascript enabled and set it to false for added security, but this is generally not necessary. We remind you that the lack of JavaScript will prevent us from viewing some sites correctly and fully, but this is also the price of security: JavaScript is probably the most used vehicle for attacking user anonymity.
- Safer still is, where possible, visit the sites of the Tor circuit, i.e. the .onion ones. These sites, being part of the circuit, do not suffer from the problem of vulnerability of the final node. Know that many "normal" sites also have an onion version, including for example Duckduckgo And Facebook. Find out if it is available for the site you are visiting and use it. Obviously you won't find the Tor version for small sites or for blogs made on subdomains, but there is a decent list of official sites that can also be reached using the onion! Here you can already find an interesting list of links (not all of them are always active): https://www.deeponionweb.com/onion-directory/.
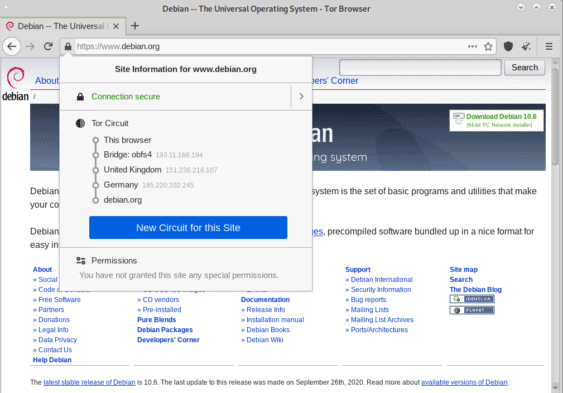
Notice how the node circuit appears with on onion sites six knots instead of three as we saw before: in this case we have the three nodes relating to the locations (with the first which can be replaced with bridges) and three others without indications which are those within the Tor circuit:
- Never log in under your own name. Tor defends anonymity: if I log in with my name, what anonymity is it? If you use an email, do so with a fictional name and using a service like Protonmail, Tutanota or a temporary service and possibly in the onion version or in any case using Tor if the onion link is not available (Tutanota does not yet have an onion version but promises to integrate it, Protonmail Yes). If you create addresses, accounts and usernames, do so using nicknames that cannot be traced back to you and NEVER use them on the clearnet. Keep these accounts for Tor browsing only. Don't even put information that could be attributable to you, such as your passions, your job, your family cat, your eating habits and so on. Tor defends you like a good bodyguard, but if you run away and walk around alone...
- Use the for function in the PC version change circuit (the nodes you connect to for the current site) and also that for change identity: with one click the Browsers it closes, deletes all the data and opens and you will have another IP. In the latter case, make sure you have done everything and remember the site or page if you need to return to it (or before changing your identity make a copy of the URL which can be pasted when restarting Tor).
- Use obfs4 bridges (optional). For those who don't know, bridges are Alternative access points for the Tor network that are not listed publicly. They are used in place of the entry node (usually referred to as a country's server) to prevent the ISP from knowing that you are using Tor. The ISP actually sees that you are using Tor even though obviously not where you are going. Bridges can make this identification not impossible but still a little less easy.
In reality, in democratic countries, bridges are generally considered superfluous: even if the ISP sees that you use Tor, the fact is essentially irrelevant. So it's up to you to decide what to do, also keeping in mind that bridges can lead to a drop in speed in some cases.
You can acquire bridges, if the Browsers has already started, since MENU> PREFERENCES> TOR> USE A BRIDGE: here you can choose those provided automatically or request them at the moment: you will be asked for a captcha and you will have your bridges ready in the field below.
If instead you want to put them at the beginning, i.e. before connecting, then click on CONFIGURE, flagged TOR IS CENSORED IN MY COUNTRY (even if it's not true, it doesn't matter) and here too you can choose them automatically from the drop-down menu; or from the official page of the site that provides the bridges (https://bridges.torproject.org/) request the bridges and copy-paste them into the appropriate field. I repeat, you will not always be invisible to the 100% but you will be more "shielded" than your ISP.
As a general rule, choose, from the available options, i bridge obfs4, which are the most recommended.
If you want to delete the bridges always go to MENU> PREFERENCES> TOR> USE A BRIDGE and simply remove the check.
This screen shows what a circuit looks like in which obfs4 bridges are used which, as you can see, take the place of the guard node that we saw before in a standard connection.
- If you need to share sensitive data, use a service like OnionShare, which uses the onion network to share securely.
To spread news, use (from Tor) a service like telegra.ph or rentry.co: these are services for publishing an article anonymously and sharing the link. The services are already anonymous by nature. Used by Tor they reach a very high level of anonymity. It goes without saying that if you spread a link from these services also on the clearnet, in addition to spreading your IP, you will make a copy that could be compared with the one published using Tor and therefore you will be more easily unmasked.
In both cases sharing the link must be done through secure channels: Signal, Telegram (for Telegram by activating the secret chat), WickrMe, Threema and similar. Avoid sharing via social media, first and foremost Facebook. Even Whatsapp, owned by Facebook since 2014, is not the best in terms of security due to metadata.
- Change your browsing habits: never use Google but use other search engines like Duckduckgo (by default on Tor), Metager, Qwant, Swisscow and similar. More generally, do not use Google services unless absolutely necessary.
- ALWAYS update Tor: each update brings both functional and security improvements, fixing bugs and placing security patches that mitigate any vulnerabilities
- Don't do P2P and torrenting. Tor is not made for this! Downloading from Torrents could involve risks, detailed in an article published on the Tor Project blog: https://blog.torproject.org/bittorrent-over-tor-isnt-good-idea
- Do not open downloaded documents such as PDFs in external applications It would seem like a minor risk, but THIS IS ADVICE NOT TO IGNORE! Even non-executable files (documents, videos, audio files, etc.) can be used to ping-back to some server on the internet and since the application that opens them does not go through Tor, you are connecting outside the network Tor. PDFs are among the documents most at risk because they are particularly rich in elements and contents within which make them suitable for hiding pitfalls
The intermediate solution, at least for PDFs, which finds an acceptable meeting point between security and usability, is to open them in Browsers Tor, although in this case JavaScript must be used which, as we know, is a potential vehicle for threats.
However, the safest and most guaranteed solution is, once the downloads have been done, to take the device offline and then open the files.
In any case, if it is not strictly necessary, avoid downloads of any kind from Tor.
- If you need to comment on a site or blog, write the text on a notepad first (like Notepad), then select everything and paste into the comment field. This reduces the chances of running into corrupted sites that may collect your writing data through keyboard typing with a keyloggers. Obviously if you already have a Linux operating system or even more so if you are operating from live by Tails (see later) you will be advantaged by the fact that it will be very difficult for your system to be infected by a keylogger. From Windows, however, you have to trust your antivirus (I still recommend Bitedefender Free edition) and hope that the PC is clean.
- Don't modify Tor Browsers personalizing it! One of the most used identification techniques is fingerprint, that is, the fingerprint of the Browsers, which in most cases tends to be unique and therefore identifiable. Tor, on the other hand, is designed to be the same everywhere and therefore less traceable. If you personalize it, you become "different" and therefore decrease the level of anonymity. For example, you'll notice that Tor starts with a small window: don't make it bigger! In fact, even the size of the screen and the resolution can contribute (not alone obviously) to filtering the results of a possible tracking attempt. But above all, don't add plugins! Tor is fine as is. So just use the internal settings and that's it. Among the advice regarding the changes not to be made I also include the language: by keeping English you will have a better result in terms of Fingerprinting, English being the most used language.
- Do not use Firefox to access .onion sites. Yes, technically it is possible, by altering a configuration parameter, to use Firefox, but I strongly advise against doing so: Tor was designed for privacy, and one of its added values is non-uniqueness and therefore a Fingerprinting generic that guarantees an excellent level of anonymity. Its structure allows you to manage the onion network completely and securely. Tor Browsers it's not just Firefox+Tor, it's much more, while if you use Firefox you risk losing all the advantages that Tor gives you Browsers.
- If possible, don't use Tor from your home network. So, this is a bit extreme advice, I realize! I include it for completeness but it is something that first of all is not so easily feasible; and then, if you are not subject to risk, it borders on paranoia. It's a bit part of the discussion we saw at the beginning about the fact that using Tor, according to certain theories, puts you under the eye of surveillance. But it has been seen that such fears are almost unfounded or in any case such a possibility should not take away our sleep.
- Don't NEVER, and I mean NEVER, get carried away by the desire to visit illegal sites, even just out of pure curiosity. The dark web, even in the most innocent people, can excite that part of the human soul that is fascinated by the slums: fight this temptation because you could find yourself in a lot of trouble! That is: if you go to a site and download a pirated book (don't do it anyway), the Carabinieri will not come knocking on your door at 5 in the morning. It's another matter if you end up on a site where drugs are sold or worse. We understood each other!
- If you want maximum use of Tor, you can use Tails, a Linux distribution based on Debian and accompanied by Tor: it is in .ISO or .img format which can be installed on DVD and USB respectively (but live versions are now used almost only on USB). Tails launches in place of the installed system using the button to change the boot order when the PC starts: from the menu select the USB on which Tails has been installed, Tails will start, your hard disk will be left out of the games and no trace will remain on the PC. On Tails Debian is modified to be able to use Tor and it is undoubtedly one of the safest ways because you don't really use the PC except as a support: the system is all on the stick, it uses Tor, it runs on RAM and the memory is, so say, to lose. the TOP! Ah, all the recommendations made above also apply to Tails. It's always about Tor. It must be said that the bridges on Tails must be configured at the beginning, in the welcome screen: once launched from the menu it will no longer be possible and to do so you will have to restart Tails from scratch.
A very interesting feature of Tails is the MAC Spoofing, i.e. the functionality, enabled by default, which masks the address of our network card, which is a sort of "license plate" that uniquely identifies our PC. With Tor installed, you must instead, if you want, enable card masking from the computer, which is something independent of Tor and whose implementation varies from system to system.
- Staying on the topic of Linux, as already mentioned, Tor is undoubtedly more secure installed on a Linux system (which distro doesn't matter) than on Windows. Or rather: Linux (and to a lesser but similar extent, MacOS) is undoubtedly more secure than Windows, which is instead very at risk of intrusions. In that case, if you don't trust Windows and don't want or aren't sure about putting Linux on your PC, Tails leaves everything out and you can browse with complete peace of mind from the USB stick.
However, remember (see installation paragraph) that Tor it can be used on Linux as if it were a portable executable, without therefore being actually installed: you download it from the official website, unzip the archive and put the folder obtained in a directory of your choice (or even in an external USB device). Then you launch Tor from the icon inside the folder and everything remains isolated.
- NOTE: the mobile version does not have, at least for now, the two separate functions "change circuit" and "change identity". The latter is equivalent to the "change circuit" of the desktop version: you will not change IP and you will not exit the Browsers. To change IP you must close and return. This is actually a feature that I hope they fix soon.
Furthermore, the mobile version does not have the ability to see the nodes from the menu next to the URL, another shortcoming that we hope is being resolved.
In general, it must be said, on mobile devices Tor does not have all the effectiveness and protection that it offers on PC.

The VPN dilemma
VPNs, especially in relation to Tor, are a problem that many have raised and many have discussed but it is very difficult to define. On average it must be said that the VPN, as it is built, It does NOT protect privacy or anonymity. VPN is mostly useful when you need to connect to a hotspot, bypass a geo-block or an ISP block in certain countries. I am not including in the discussion the so-called corporate VPN which is the system that companies use to make those who are far away work remotely, in the company's internal network, as if they were physically in the office.
Let's look at the critical issues relating to VPN services.
The problem with VPNs is that on the one hand you have to trust the supplier and on the other hand that often the most blatantly commercial VPNs they tell inaccurate things on the role of their service and omit what would otherwise not allow them to sell as they do. Sometimes they lie or tell half-truths. Sometimes there are apparently independent sites that lie through their teeth.
In essence and simplifying to the bare bones, a VPN is a tunnel that encrypts the connection from our connection to the VPN server, but when the connection goes out, obviously, it must be decrypted, otherwise the site server (as has already been seen in Tor) does not "understand" and we cannot connect. But many VPNs simply say that “the connection is encrypted” and even the diagrams and diagrams they show are often misleading because it really looks like everything is encrypted, which is not true because it is not technically possible. And if the connection is not secure, i.e. it is not https, you are still not protected. Briefly summarized, the VPN works like this (#=encrypted; >=not encrypted):

It's true that the VPN's IP comes out of the VPN and not ours, but it is not true that the connection, as many implicitly imply, is entirely encrypted.
Even the so-called politics of no-logs is half true: the servers must retain something, otherwise the management of the service would not be possible. Some VPNs are transparent and tell you what they keep and what they don't, so one can adjust. But even when they don't actually keep the IP and the sites visited, the IP (for reasons that I won't specify) is no longer indicative to the 100% and is no longer the only element so decisive for tracking. There is for example, as we have already seen, the Fingerprinting and there are other elements that are much more used to track users.
There are, I repeat, honest VPNs that are more reliable and actually tell what they do, but in any case the VPN adds practically nothing to Tor.
Indeed, to be honest, adding a VPN increases your attack surface which instead must be reduced to a minimum. In computer security, the rule that simplicity pays applies: secure systems are not created by increasing complexity, which does not offer any additional security through the logic of "it doesn't decrease security anyway".
Some VPNs even have pre-built servers to browse directly on Tor without Tor Browsers but using Firefox. A terrible idea, in my opinion.
In the end, a VPN, no matter how reliable, Open source and “secret”, it is still a commercial activity and above all a third party that you replace your ISP. Not that the ISP is necessarily a more reliable entity, but by shifting our trust to the VPN, our situation changes very little: the certainty that the service will behave better than the ISP does not exist. Among other things, a company can always have economic problems that affect the quality of the service, just like any other company.
Tor, on the other hand, is free software and, very importantly, DECENTRALIZED: it does not have specific servers to attack that could put the entire network in crisis: between nodes and bridges Tor exceeds the figure of 8000 and even if there are nodes controlled by governments, hackers or whoever on their behalf, it will still be more difficult to attack and it is practically impossible to tear down the entire net. A VPN, on the other hand, has servers that are more identifiable and can be an easier target.
So basic Tor doesn't need a VPN. If you really want to test it, the most common solution is to launch the VPN and then launch Tor, also called solution Tor over VPN, why do the opposite (VPN over Tor), that is, running a VPN inside Tor is much more complex and requires technical skills or the provider to provide that service. But neither one nor the other solution gives great additional advantages. Furthermore, the second solution, VPN over Tor, precludes access to onion sites.
It's more the illusion that the more stuff you put on, the better, but that's not the case.
Plus there's the fact of payment: unless you pay in cryptocurrency using a connection other than yours or with cash delivery (some services include this option), there will always be a trace of your payment, which is anything but anonymous and risks revealing who you are.
Summing up: Should VPNs be banned entirely? Absolutely not. For example, if you need to torrent, if you need to get around a geoblock or if you use hotspots or open networks a lot, then a good VPN can help you. But if you're looking for more anonymity, perhaps by adding it to Tor, then I don't recommend it.
If you want advice outside of advertising logic on the most reliable VPNs, visit https://www.privacytools.io/providers/vpn/ (PrivacyTools has taken a turn that not everyone likes, for example it has started sponsoring VPNs that are not strictly privacy-friendly like NordVPN. You can also and above all take a look at VPNs present on PrivacyGuides skariko note). Some data (for example on the number of servers) are not always up to date but the guide is still valid.
Guide to using Tor Browsers: conclusions
Tor it's perfect? Far from it! Being de-anonymized is possible and technically feasible. NSA, CENTRAL INTELLIGENCE AGENCY, FBI, telecommunications police around the world are always working to find illicit activity on Tor. And they often succeed! But the question is: are we subjects of interest to the police? Are we criminals? Do we conduct illegal activities that arouse the interest of law enforcement? Well, the answer comes by itself.
Of course, surveillance also concerns honest people. Tor also defends our right not to always have an eye on us, examines and catalogs our every movement and this can constitute a problem: Privacy is a right that regardless of whether or not we do illegal things and the famous "I have nothing to hide" is not valid and has no meaning: going to the bathroom is not illegal but we want to do it with the door closed, right?
Unfortunately, perfection is not of this world and we can in no way be sure of being observed while on Tor. I said "observed" and not indicted, but this too remains a significant problem. It is even said (but the rumors circulating on the web always need to be considered) that the NSA keeps under observation those who use Tor or those who are interested in it in general or, even further, those who deal with privacy and related tools: VPN , proxies, etc. All this can be annoying, of course, but as we know well, our right to privacy and anonymity ends the moment we are not connected via our PC, but when we live in this era where, between bank cards, points cards, cameras, GPS and digitized documents we are necessarily under the eye of surveillance from which it is impossible to escape. What we can do is strive for an ideal that brings us as close as possible to the goal we have set for ourselves. And to do this, Tor is without a doubt one of the most powerful tools.
These are all useful notions for those who want to use Tor, both to protect their anonymity and to visit sites that cannot be accessed on the "normal" web. Happy sailing and... keep your guard up!
Guide to using Tor Browsers: some important links
Tor project: https://www.torproject.org/
Tails: https://tails.boum.org/index.it.html
- Tor on Wikipedia[↩]
- Slicing onions: Part 1 – Myth-busting Tor.[↩][↩]
Join communities
If you have found errors in the article you can report them by clicking here, Thank you!